Prerequisites
Prerequisites
- An Enkryptify workspace with admin access
- A Google Cloud project
- Permissions to create a Service Account and grant IAM roles in the project
Permissions
Permissions
Enkryptify connects to your GCP project using Service Account impersonation. You create a Service Account in your project with Secret Manager permissions, then grant Enkryptify the ability to impersonate it.
- On your target Service Account the sync needs:
secretmanager.secrets.createsecretmanager.secrets.deletesecretmanager.secrets.getsecretmanager.secrets.listsecretmanager.versions.add
- On the same Service Account:
Service Account Token Creator(roles/iam.serviceAccountTokenCreator) to principalenkryptify@enkryptify.iam.gserviceaccount.com
The impersonated Service Account does not have secretmanager.versions.access, so it cannot read secret payloads from GCP. Enkryptify only writes versions and reads metadata. Secret values are never fetched from GCP.
Steps to complete
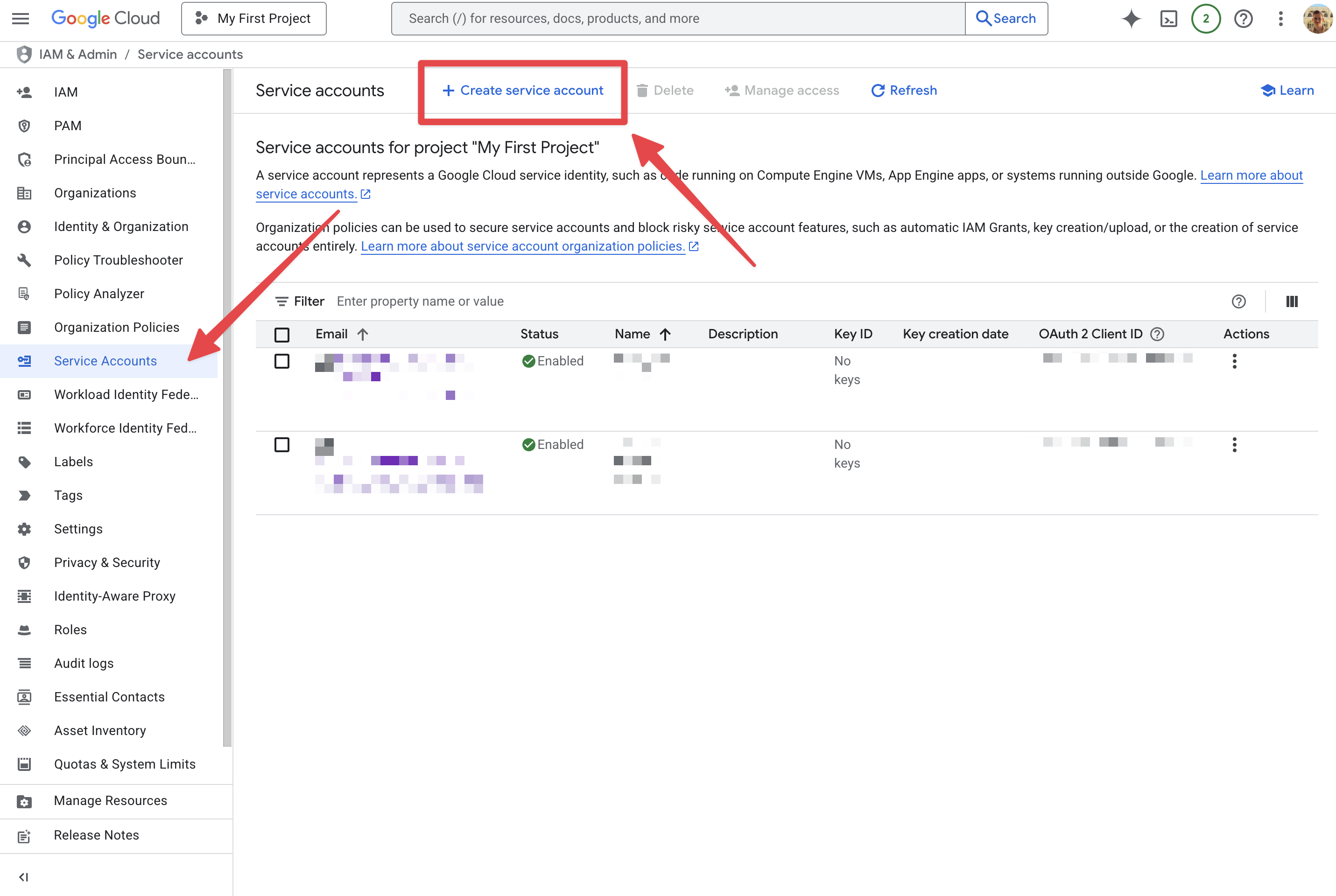
Create a Service Account (GCP Console)
- Navigate to IAM & Admin → Service Accounts.
-
Create a new Service Account with an ID of your choosing.
Grant Secret Manager permissions to the Service Account
- Create a new role with the following permissions (recommended):
secretmanager.secrets.createsecretmanager.secrets.deletesecretmanager.secrets.getsecretmanager.secrets.listsecretmanager.versions.add
- OR use the following role:
-
Secret Manager Admin(roles/secretmanager.admin)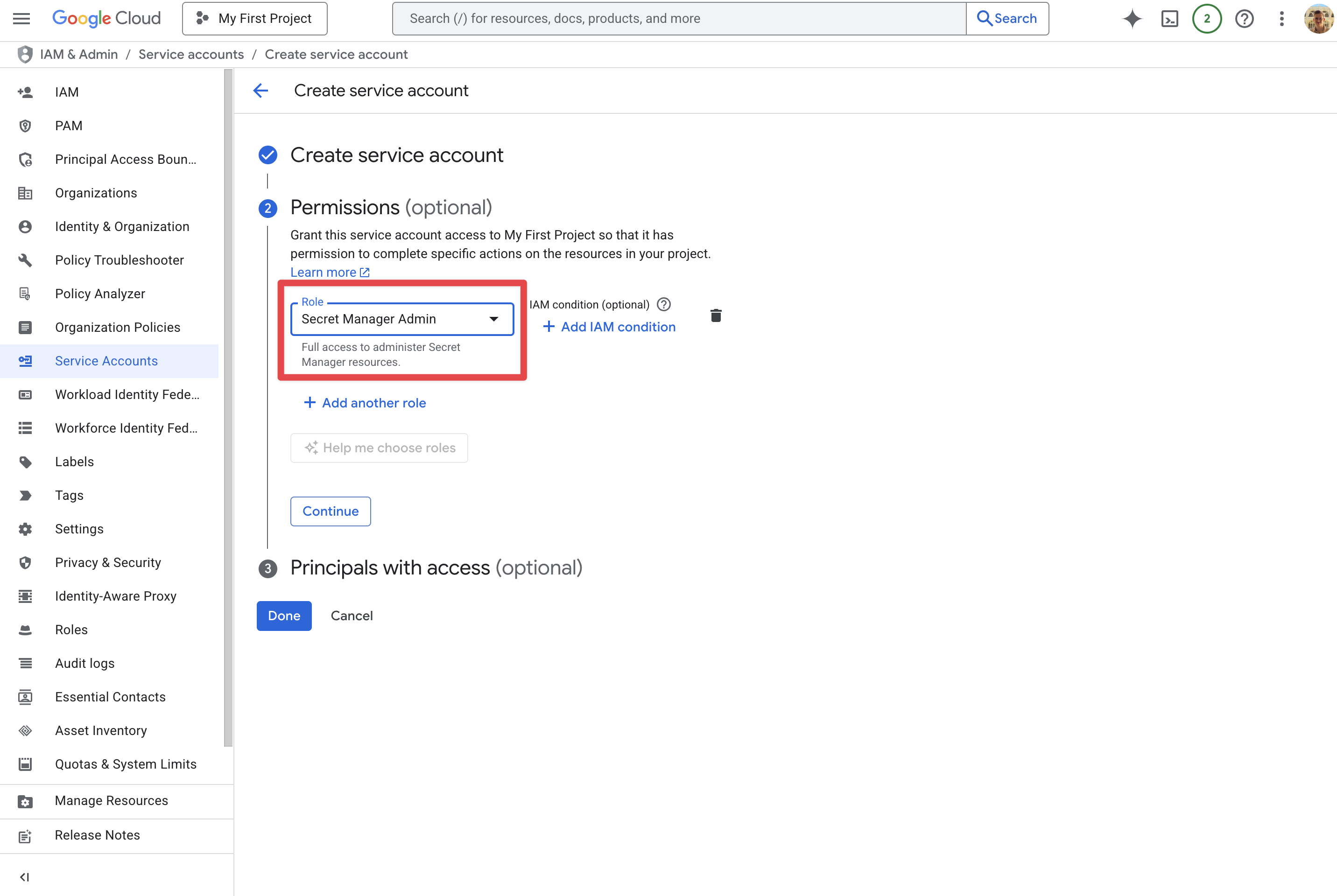
-
Enable Service Account impersonation
- Grant
Service Account Token Creator(roles/iam.serviceAccountTokenCreator) toenkryptify@enkryptify.iam.gserviceaccount.comon your Service Account.-
Open the Service Account →
Principals with accesstab → Grant Access → add the principal and role.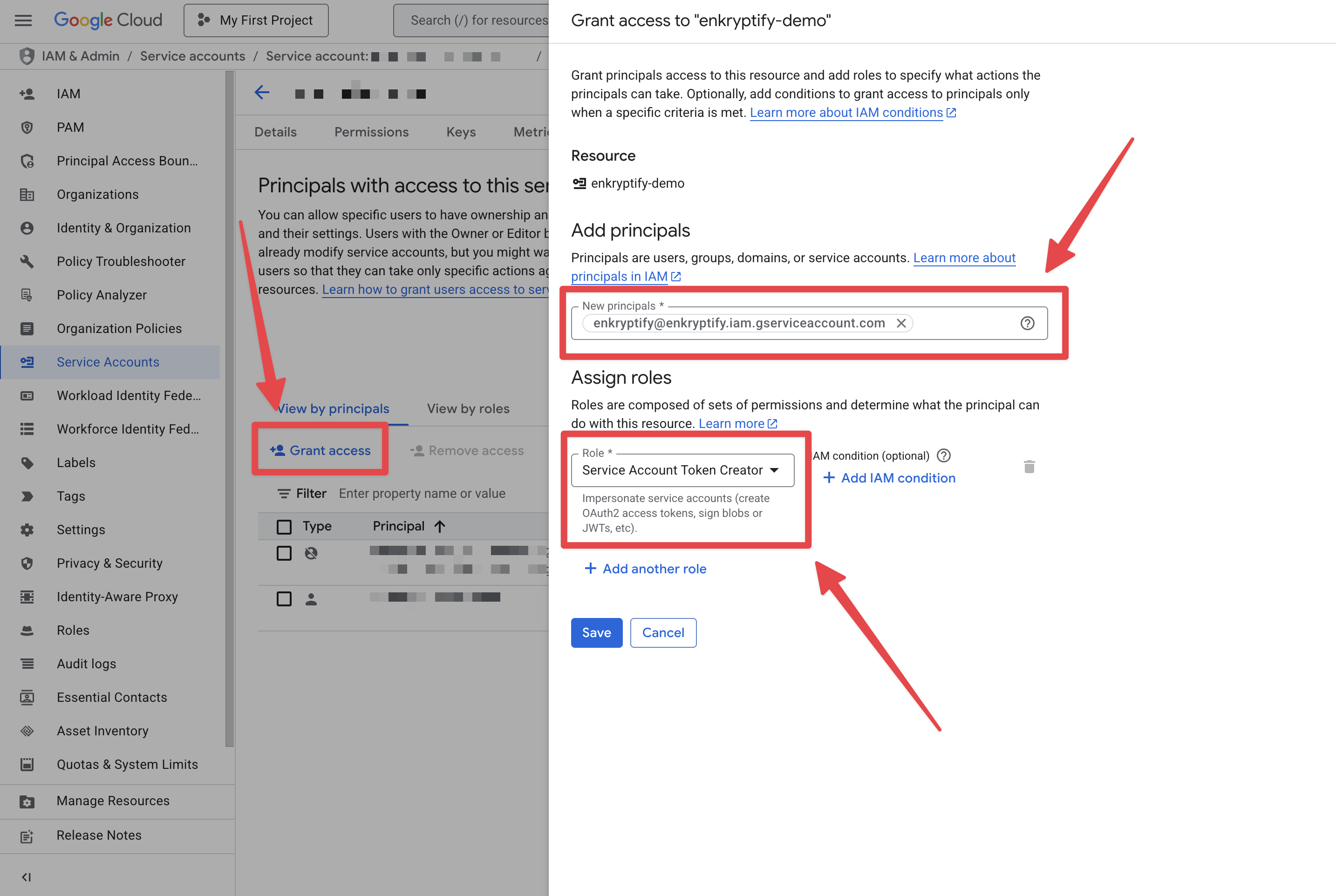
-
Open the Service Account →
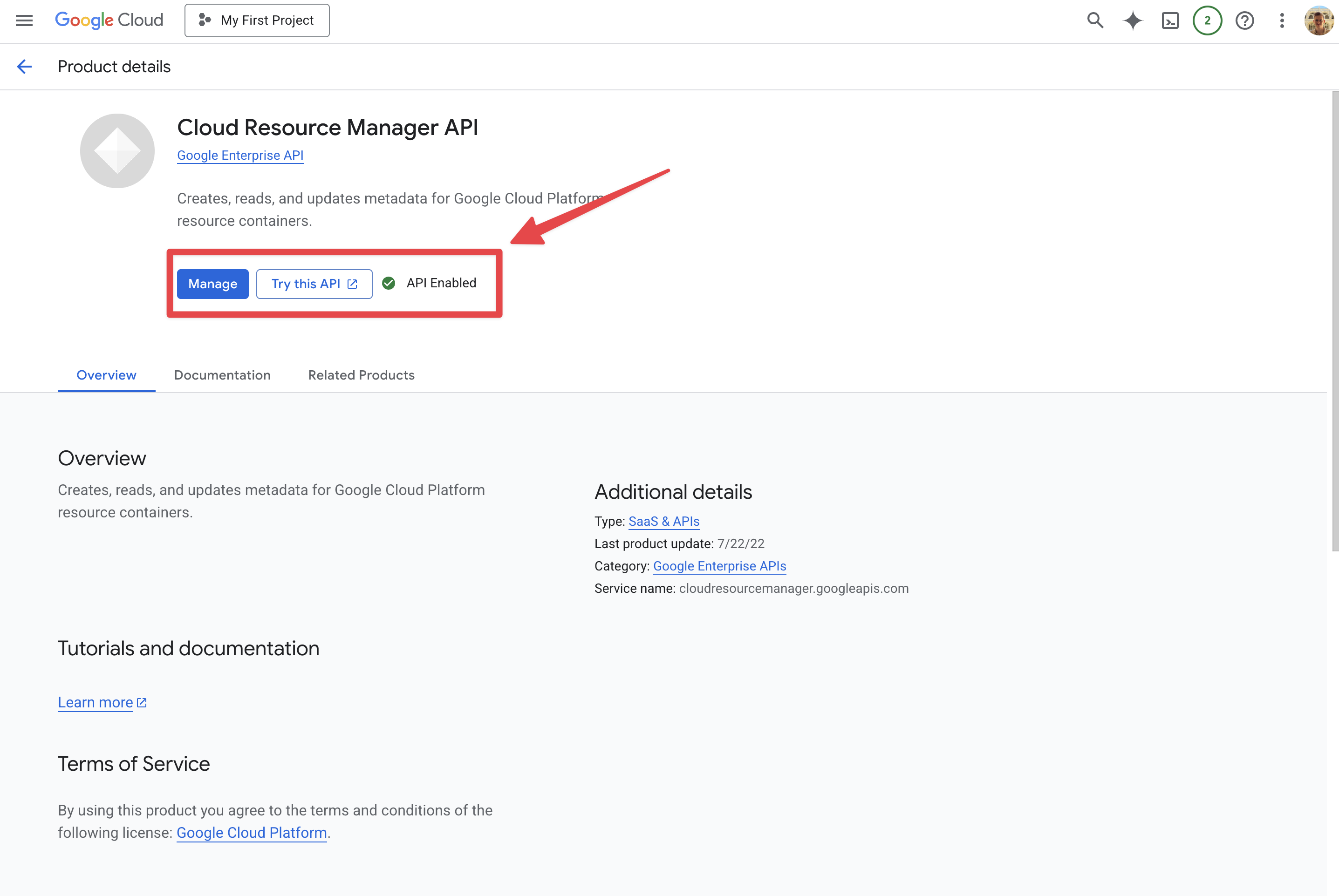
Enable required APIs
- Ensure these APIs are enabled on your project:
- Cloud Resource Manager API
- Secret Manager API
-
Service Usage API
Authenticate in Enkryptify
- In Enkryptify, enter your
Project IDand the Service AccountEmailto impersonate.